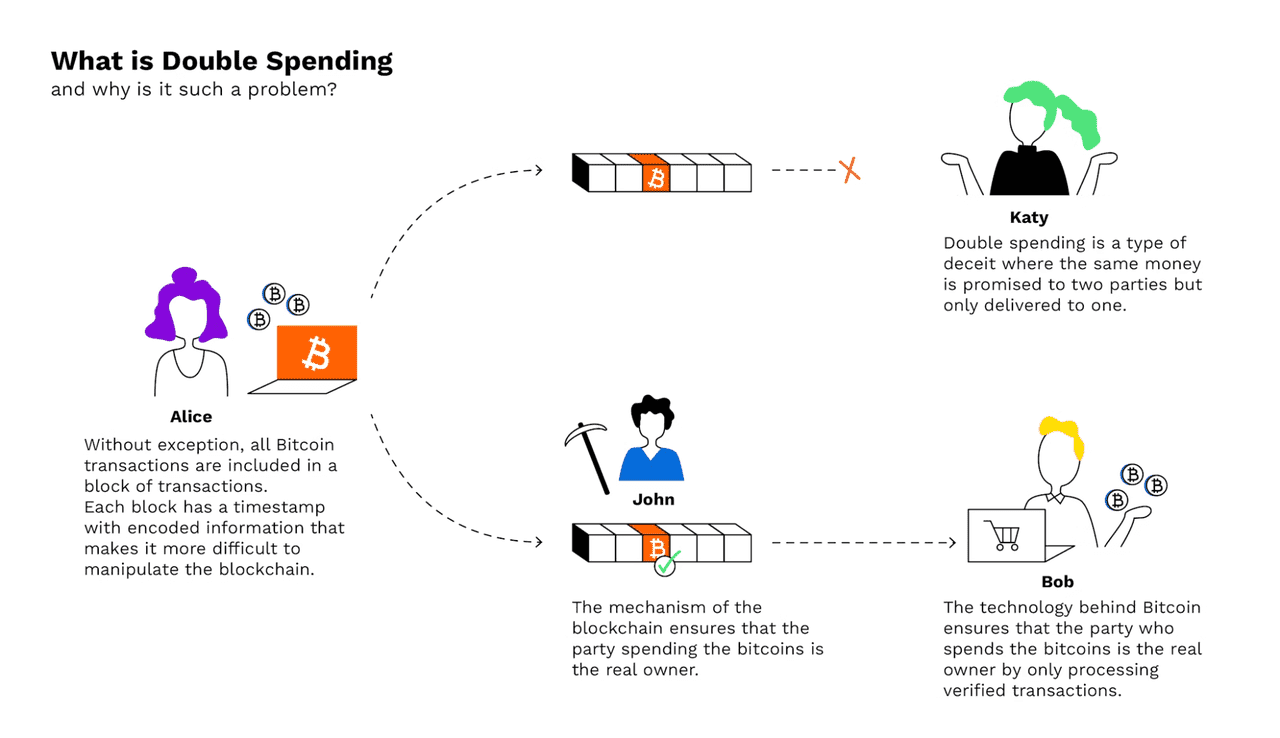
Double-spending refers to the risk in digital currency systems that the same money can be spent more than once. In the physical cash world, this isn’t an issue – if you hand someone a $10 bill, you no longer have that bill to spend again. But with digital money, a token is essentially just data, which could be copied or reused if not properly controlled. Early digital cash experiments struggled with this problem: how to prevent a user from duplicating a digital token and spending it twice? The traditional solution in centralized digital payment systems is to use a trusted authority (like a bank) to verify each transaction against a ledger and update balances. However, Bitcoin, as a decentralized network, cannot rely on any single authority – it needs to solve double-spending in a trustless manner.
When Satoshi Nakamoto invented Bitcoin in 2009, the revolutionary achievement was to devise a workable solution to the double-spend problem without any central gatekeeper. Bitcoin’s blockchain mechanism, enforced by a network of miners and nodes, ensures that once a bitcoin is spent in one transaction and confirmed in the blockchain, it cannot be spent again in another. In over 16 years of Bitcoin’s operation (2009–2025), there have been no confirmed incidents of a malicious double-spend on the main Bitcoin network. Bitcoin’s design makes double-spending extremely difficult – as of 2025, with the network’s massive size and security, attempting a double-spend is practically futile. Below, we explain what double-spending is, how Bitcoin prevents it, the types of attacks related to double-spending, and real-world cases (and misconceptions) regarding this issue.
How Does Bitcoin Prevent Double-Spending?
Bitcoin prevents double-spending through public ledger transparency, consensus rules, and proof-of-work mining. The Bitcoin blockchain is a public ledger that records every transaction, with each full node holding a copy and updating it as new blocks are added. This transparency allows anyone to verify if a coin has already been spent, making double-spending evident through conflicting entries.
Transactions are confirmed only when included in a block that miners agree upon. For example, if Alice pays Bob 0.1 BTC, her transaction enters the mempool and is picked by a miner to be included in a block. The miner then solves a cryptographic puzzle to validate the block, which is verified by other miners. Once confirmed, Bob's receipt is part of the blockchain.
The longest valid chain establishes the authoritative history, making it extremely difficult for an attacker to create an alternate version without more mining power than the honest network. After about six confirmations, the likelihood of a successful double-spend becomes nearly zero.
Additionally, every Bitcoin’s history is traceable. Each new transaction consumes unspent outputs from previous ones. If two conflicting transactions are detected, only the first valid one is accepted. This first-seen rule, along with the miners’ cost in electricity to add blocks, makes it impractical to reverse confirmed transactions. Overall, Bitcoin's system ensures that double-spending is either immediately caught or requires a prohibitively expensive attack to alter the ledger.
The Double-Spending Problem Explained
To clarify the double-spend problem, let’s walk through an example. Imagine Alice has 1 BTC and wants to trick two parties into both accepting the same coin. She sends Transaction 1: “Alice pays 1 BTC to Bob” and also prepares Transaction 2: “Alice pays 1 BTC to Charlie” (spending the same coin). She broadcasts Transaction 1 to Bob, and Bob, seeing it arrive in his Bitcoin wallet, trusts that he will get 1 BTC (perhaps Bob hands Alice the product at this point). If Bob is being cautious, he will wait for this transaction to be confirmed in a block. Meanwhile, Alice also broadcasts Transaction 2 (perhaps with a higher mining fee) to try and get that one confirmed instead of the first. This is a double-spend attempt – only one of these transactions can ultimately end up valid, because they use the same input coins.
In the normal course of events, miners will include one of these transactions in a block. If Transaction 1 gets confirmed first, the network will reject Transaction 2 as invalid (its inputs are already spent). If instead Transaction 2 somehow gets confirmed in the blockchain before Transaction 1, then Bob’s transaction would be the one rejected. The key point is that both transactions cannot coexist in the ledger. Bitcoin’s consensus ensures one history wins. From Bob’s perspective, the risk is if he accepted Alice’s payment and gave her the goods before the transaction was securely confirmed, a sneaky Alice could try to make a conflicting transaction take precedence.
Bitcoin’s recommendation is that high-value transactions wait for multiple confirmations. The more blocks that are mined on top of a transaction, the more secure it is. This is because an attacker would have to redo the proof-of-work for that transaction’s block and all succeeding blocks to change the history – an effort that grows exponentially harder with each additional block. After about 6 blocks (roughly 1 hour), the community regards a Bitcoin transaction as practically irreversible.
What is Double Spending
Types of Double-Spend Attacks
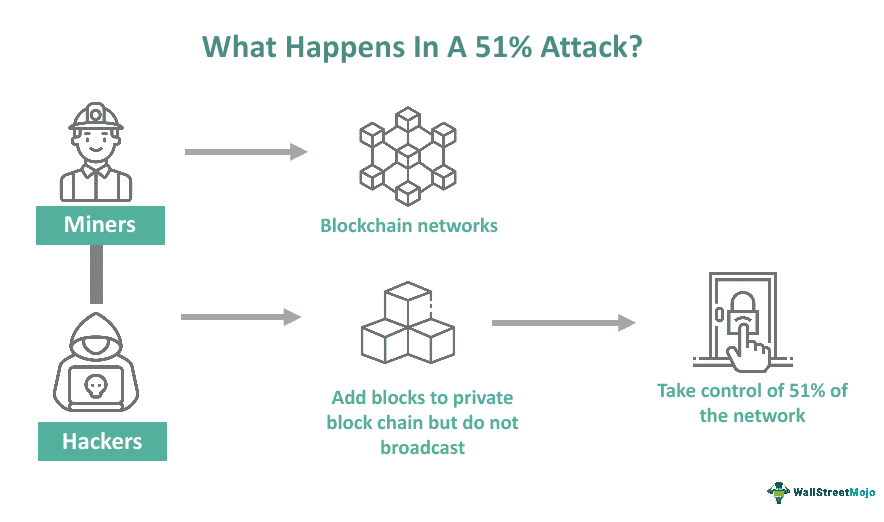
1.The 51% Attack (Majority Attack)
A 51% attack is often discussed as the most brute-force way to double-spend: an attacker obtains control of over 50% of the total network hash power (computing power) and uses that majority to outpace other miners in producing blocks. If an attacker can consistently mine blocks faster than the rest of the network, they could fork the blockchain and make their own version of the ledger the “longest chain.” In doing so, the attacker could include (or exclude) transactions at will – for instance, they could spend 0.1 BTC to Bob on the public chain, then secretly mine an alternate chain where that transaction never happened, instead keeping the 0.1 BTC. Once their secret chain is longer, they release it, and nodes switch to this new longest chain where Bob’s transaction is absent (thus effectively “double-spending” the coin).
In practice, a 51% attack on Bitcoin is extraordinarily difficult. Bitcoin’s hash rate (the combined mining power of the network) is now immense – on the order of hundreds of exahashes per second (approximately 10^18 hashes per second). By October 2025, Bitcoin’s network hash rate was recorded around 1 zettahash (10^21 hashes) per second, a record high. Gaining majority control of this would require an attacker to own or hijack an unprecedented amount of mining equipment and electricity. The cost would be astronomical, likely billions of dollars, far outweighing any potential gain from double-spending. This is why no one has ever successfully executed a 51% attack on Bitcoin. Furthermore, Bitcoin’s mining community is decentralized among many independent pools and miners – even the largest mining pool typically controls only 20-25% of hash power, and historical cases when a pool approached 51% were met with voluntary throttling to maintain trust.
However, other smaller proof-of-work cryptocurrencies have experienced 51% attacks leading to double-spends. For example, Ethereum Classic (ETC) suffered multiple 51% attacks in 2020, where attackers reorganized the blockchain and double-spent coins, undermining confidence in that network. Similarly, Bitcoin Gold (BTG) (a Bitcoin fork) was hit by 51% attacks in 2018 and again in 2020. These incidents happened because those networks had a relatively low hash rate (making them vulnerable) and significant value to steal, allowing attackers to rent or acquire enough mining power to temporarily surpass honest miners. In one August 2020 Ethereum Classic attack, attackers were able to double-spend an estimated $5 million worth of ETC. The Bitcoin network, by contrast, is so large that renting enough hash power is not feasible – there simply isn’t enough spare Bitcoin mining capacity available for hire, and buying that many machines and energy outright is prohibitively expensive.
In summary, the 51% attack remains a theoretical double-spend method on Bitcoin but is practically a non-issue given Bitcoin’s scale. It’s a greater concern for smaller coins. Bitcoin’s defense against it is its sheer mining power and the economic game theory that miners have more to gain from mining honestly than from attacking the network (an attack would likely crash the Bitcoin price and thus the value of the attacker’s rewards).
Bitcoin 51% Attack (source)
2.Race Attack (0-Confirmation Double-Spend)
A race attack is a double-spending method where the attacker swiftly sends two conflicting transactions into the network, hoping one goes to the victim and the other gets mined first. It typically targets fast payments where the receiver might accept a transaction with zero confirmations. For instance, Alice pays Bob 0.1 BTC in Bob’s store and Bob sees the unconfirmed transaction on the network. Simultaneously (or shortly after), Alice broadcasts a second transaction sending that same 0.1 BTC back to herself (to another address she controls), likely with a higher fee to entice miners. If Bob hands goods to Alice immediately after seeing the unconfirmed transaction, he’s at risk – Alice’s goal is for the second transaction to win the “race” and be included in a block instead of the first. If miners confirm Alice’s self-payment, Bob’s transaction becomes invalid (double-spent) and never confirms. Alice would leave the store with Bob’s goods and also still have her 0.1 BTC (because the payment to Bob never actually gets finalized).
The race attack scenario is why Bitcoin best practices urge sellers to wait for confirmations for anything of significant value. With no confirmations, a transaction is not yet part of the blockchain and thus not secure – it’s just floating in the mempool and could be replaced. Bitcoin’s network has a feature called Replace-By-Fee (RBF) which, if enabled, allows a sender to rebroadcast a transaction with a higher fee, effectively replacing the original in the mempool. RBF is useful for bumping fees, but it also means one should be cautious: if you accept a 0-conf Bitcoin transaction that had RBF enabled, the sender can potentially fee-bump a double-spend transaction to override it. Many wallet software mark 0-conf transactions as untrusted for this reason.
Bob can protect himself by waiting for at least one confirmation (preferably more for larger amounts). Once Alice’s payment is in a block, a conflicting transaction will be rejected by the network as its inputs are already used. In the race attack, speed is the weapon of the attacker — they rely on the merchant’s haste. If the merchant waits until mining has occurred, the attacker’s window closes. Therefore, race attacks are only viable on parties that accept payments instantly on seeing them in the mempool (common with some fast retail scenarios or services that foolishly accept 0-conf). Some projects have tried to create secure zero-confirmation schemes for Bitcoin (such as Bitcoin Cash’s approach to instant transactions), but on Bitcoin mainnet the safest route is still to wait for confirmations.
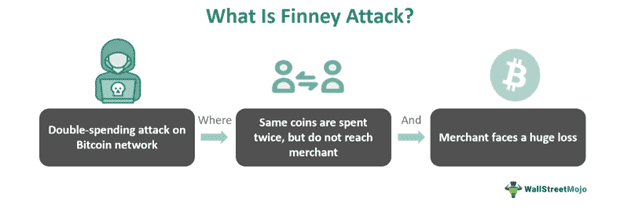
3.Finney Attack
A Finney attack is a more technical and timing-based double-spend, named after early Bitcoin developer Hal Finney. In this scenario, the attacker pre-mines a block that contains a transaction sending coins to themselves, but they don’t broadcast this block immediately. Let’s illustrate: Alice (the attacker) pre-mines a block that includes a transaction of 0.1 BTC from Alice to Alice’s own second address. She holds this block without broadcasting it. Now Alice goes to Bob’s store and makes a payment of 0.1 BTC to Bob (a regular transaction, not in a block yet). Bob sees the transaction and perhaps after a single confirmation (just to reduce obvious races) he lets Alice take the goods. Here’s the trick: Alice now quickly broadcasts the pre-mined block she was holding. If her block is valid and beats other miners to be accepted, the network will see that block as part of the longest chain. In Alice’s block, the 0.1 BTC was sent back to herself prior to the transaction with Bob. That means when the network tries to add the transaction paying Bob, it conflicts – those coins were already spent (to Alice’s other address) in the block Alice mined. Bob’s transaction thus never gets confirmed; it’s invalidated by Alice’s published block. Bob loses the 0.1 BTC payment he thought he had, and Alice’s 0.1 BTC never truly left her control (it went to another address she owns in the pre-mined block).
The Finney attack is difficult to pull off today because it requires mining a valid block, which is probabilistic and expensive, and also careful timing. It only works if the merchant accepts a payment on very few confirmations (ideally zero). If Bob waits 6 confirmations, Alice cannot Finney attack him unless she can mine 6 consecutive blocks in secret, which is effectively the 51% attack scenario again. Finney attacks were more of a conceptual concern in Bitcoin’s early days when hash power was low and a single CPU miner might stumble on a block and attempt something sneaky. In the modern Bitcoin network with specialized miners and mining pools, the odds of a successful Finney attack by an ordinary user are astronomically low. It’s largely a theoretical risk that underscores the same lesson: don’t trust transactions until they’re sufficiently confirmed.
Finney Attack (source)
Has Bitcoin Ever Had a Double-Spend Incident?
News about potential "Bitcoin double-spends" occasionally causes confusion, but Bitcoin's ledger has never been undermined by a confirmed double-spend attack. An example occurred on January 22, 2021, when BitMEX's tool flagged what seemed like a $21 double-spend. This incident led to a brief dip in Bitcoin's price due to fears of compromised integrity. However, it was a stale block and a replaced transaction, not a true double-spend.
In this case, a user with a stuck low-fee transaction broadcasted multiple higher-fee transactions. Two miners included different versions in blocks almost simultaneously, creating a temporary blockchain fork. Eventually, one block was chosen, and the other became orphaned, leading to both double-spend attempts being invalidated. The consensus rules ensured only one transaction could be confirmed, illustrating that conflicting transactions don't equal a network failure.
Additionally, aside from historical misreports, Bitcoin has shown resilience against double-spending. The only noted issue was the August 2010 "value overflow incident," a software bug quickly rectified. In contrast, smaller networks like Bitcoin SV have experienced actual double-spend attacks.
The takeaway is that Bitcoin's decentralization and proof-of-work security effectively protect against such attacks. By October 2025, Bitcoin's vast market cap and mining power made it highly resistant to double-spends, as the costs of an attack would far outweigh any potential benefits. Miners have a greater incentive to act honestly and maintain trust in the system.
Conclusion
Bitcoin was the first digital currency to solve the double-spending problem in a decentralized manner, successfully preventing true double-spend attacks. Its blockchain, secured by proof-of-work, links each block to the previous one, creating significant computational costs for would-be attackers. Bitcoin's security is strongly linked to its high hash power and decentralization, making it the most secure cryptocurrency, with its network hash rate hitting all-time highs in 2025.
While theoretically vulnerable, Bitcoin's economics and game theory effectively deter attacks. Honest miners earn billions while attackers would need to spend comparable amounts to steal far less, risking Bitcoin's price collapse. Users can mitigate double-spending risk by waiting for transaction confirmations; the community norm of six confirmations ensures security for most use cases.
Although edge cases may cause brief blockchain forks, Bitcoin's consensus protocol quickly resolves these issues, maintaining a single source of truth. This resilience has made Bitcoin a trusted means of transferring value globally. With growing network security and community vigilance, Bitcoin is likely to remain immune to double-spending, showcasing a robust solution to a long-standing problem in digital currency.