Bitcoin is often praised for its strong security, but you may have heard of the term “51% attack” – a scenario where someone could theoretically take over the Bitcoin network. In this guide, we’ll explain what a 51% attack is, how it works, and whether Bitcoin could ever be hacked in this way. We’ll also look at real-world examples from other cryptocurrencies and discuss why Bitcoin has remained safe so far. As of September 2025, has Bitcoin ever suffered a 51% attack? What would it take to do so? Read on to get answers in simple terms.

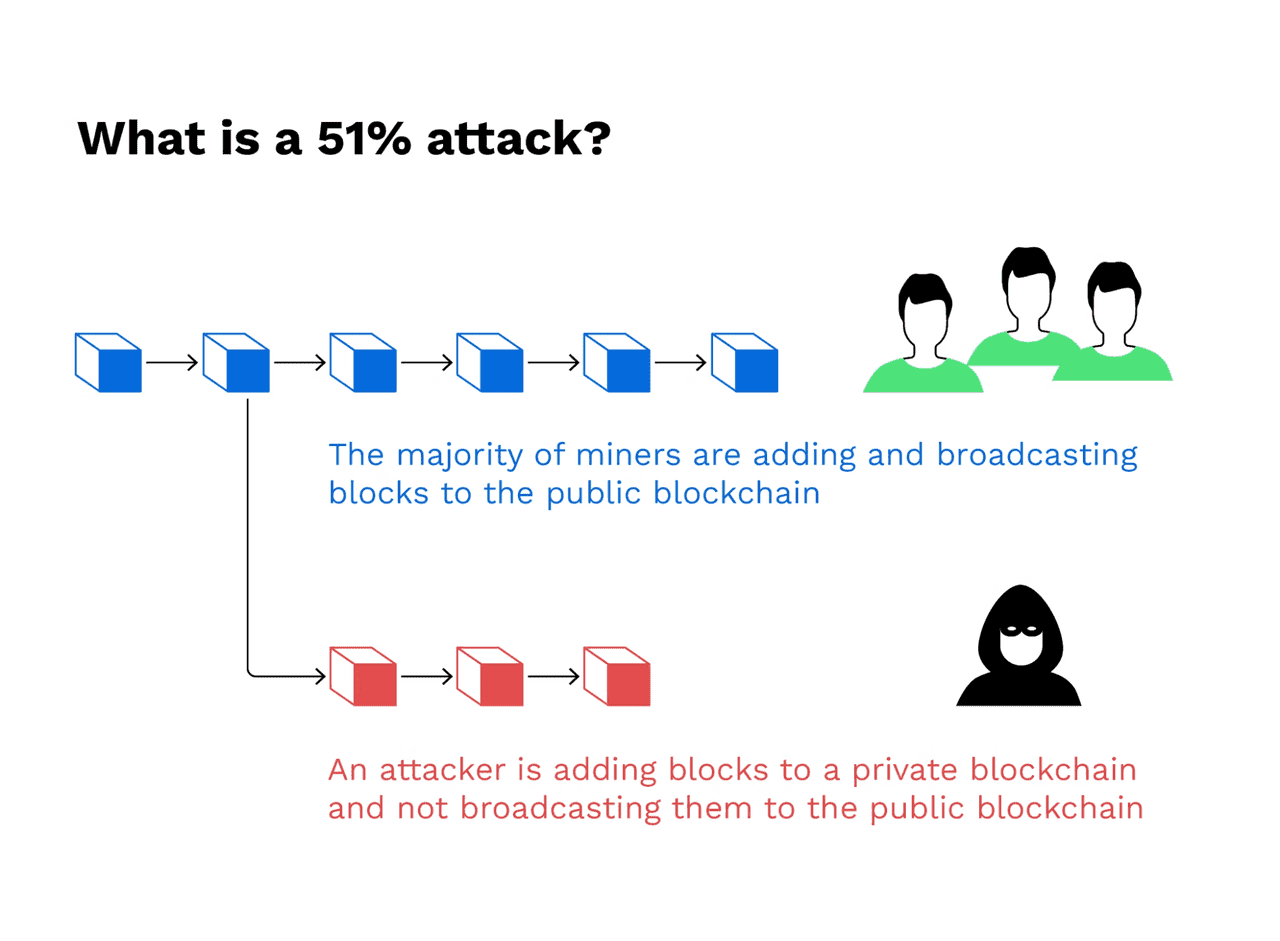
What is a 51% Attack?
A 51% attack, sometimes called a majority attack, is an attack on a blockchain where a single malicious actor or group gains control of more than 50% of the network’s mining power (hash rate). By controlling the majority of the computational power, the attackers can then dominate the process of adding new blocks to the blockchain. This control can allow them to do dangerous things like:
-
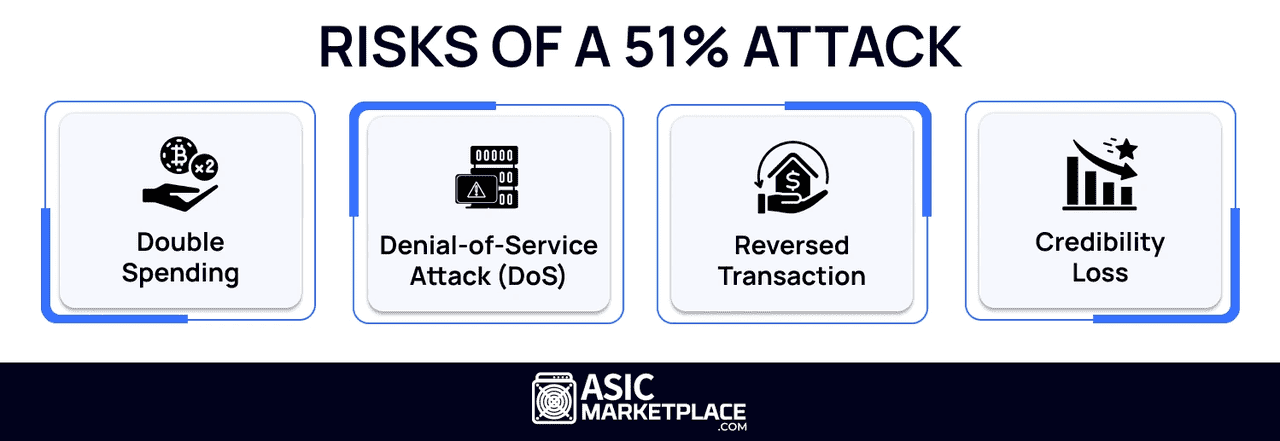
Double-spending coins: They could spend coins, then secretly create an alternate version of the blockchain where those transactions didn’t exist, essentially spending the same coins again. This is the primary motivation of a 51% attack – to falsify transactions for financial gain.
-
Blocking or reversing transactions: With majority power, attackers could prevent other miners’ blocks from being confirmed, or even rewrite recent blocks. They could stop certain transactions from being added to the blockchain, or change the order of transactions.
-
Control over new blocks: The attackers could mine blocks faster than the rest of the network, meaning they get most of the block rewards and fees, and they dictate the “true” chain (since the longest chain wins in Bitcoin’s consensus).
However, what a 51% attack cannot do is also important to note: Attackers cannot steal coins directly from wallets (they can only affect transactions in transit). They also cannot change the rules of the protocol (for example, they can’t arbitrarily create new coins beyond the fixed Bitcoin supply) – those things are enforced by the network’s nodes and cryptography. The attack primarily affects transaction history and trust.
In summary, a 51% attack compromises the integrity of a blockchain’s ledger by letting a malicious party temporarily override the consensus. It’s a bit like if someone could rewrite the last chapter of a shared history book because they control more than half of the editing power.
How Would a 51% Attack on Bitcoin Work?
To execute a 51% attack on Bitcoin, an attacker would need control of over half of its hashing power, which secures the network through Proof-of-Work (PoW). Here’s a brief overview of how such an attack could occur:
-
Gaining Majority Hash Power: The attacker would need to acquire more than 50% of the Bitcoin hash rate, which, as of 2025, is in the range of hundreds of exahashes per second (EH/s). This would require massive investment in mining hardware or subverting existing miners or pools.
-
Mining a Secret Chain: With majority hash power, the attacker could secretly mine their own blocks, creating two blockchain versions: a public one with their transactions and a hidden one without them.
3. Outpacing the Honest Chain: By mining faster than the honest chain, the attacker can create a longer chain, which Bitcoin's rules dictate as the valid one.
4. Releasing the Malicious Chain: The attacker then broadcasts this longer chain, forcing honest nodes to switch. This effectively rewinds previous transactions, allowing double-spending.
5. Implications: Victims of the original transactions will find that those payments never occurred, enabling the attacker to retain both the goods and the coins.
While the mechanics sound alarming, achieving a 51% attack on Bitcoin is extremely impractical due to:
-
High Hash Power Requirement: Gaining 204 EH/s of power would require billions of dollars in hardware and enormous electricity usage.
-
Logistical Challenges: The massive effort needed to obtain and operate many miners would be highly noticeable.
-
Community Defense: The Bitcoin network has measures to counteract such attacks, including monitoring mining shares and implementing emergency upgrades if necessary.
Ultimately, even a short-lived attack would damage confidence in Bitcoin.
51% Attack Explainer
Has Bitcoin Ever Been 51% Attacked?
Bitcoin itself has never suffered a successful 51% attack in its history. The network, since its launch in 2009, has grown so robust that no attacker has been able to control a majority of its hash power, even briefly. There have been a couple of notable close calls or warnings:
-
GHash.io incident (2014): GHash.io was a mining pool that, at one point in 2014, garnered roughly 50% of the Bitcoin network’s hash rate. This wasn’t a malicious attack; it was just a very popular pool that many miners pointed their hardware to (likely because of good rewards and 0% fees). When the community realized one pool had so much power, it raised alarms about the theoretical risk of a 51% attack. In response to community pressure and their own sense of responsibility, GHash.io voluntarily pledged to keep its share below 40% and even asked miners to switch away to decentralize the hash power. This showed the community’s commitment to preventing any single entity from reaching majority control. Eventually, GHash.io’s dominance subsided (and the pool is no longer around today). The 2014 incident is often cited to illustrate that even approaching 51% is considered unacceptable in Bitcoin’s culture.
-
Foundry USA & AntPool (2025): In mid-2025, two of the largest Bitcoin mining pools – Foundry USA and AntPool – together accounted for just over 50% of the global hash rate for a brief period. This was a combined statistic (around 30% with Foundry and 20% with AntPool), not a single actor, but it sparked new discussions on centralization risk. Importantly, these two pools are operated independently, and each pool consists of thousands of individual miners. The likelihood of them colluding to attack the network is extremely low, as it would require convincing many participants to act against their own interests (destroying Bitcoin’s trust would crash its price, hurting those very miners). After community discussion, the situation somewhat improved as more hash power flowed to smaller pools. This incident reinforced awareness but was not an actual attack – just a concentration that people are keeping an eye on.
Outside of these, Bitcoin has remained secure. The sheer scale of Bitcoin’s mining network has so far protected it from any 51% takeover.
It is worth noting that other cryptocurrencies have suffered 51% attacks, especially those with smaller networks:
-
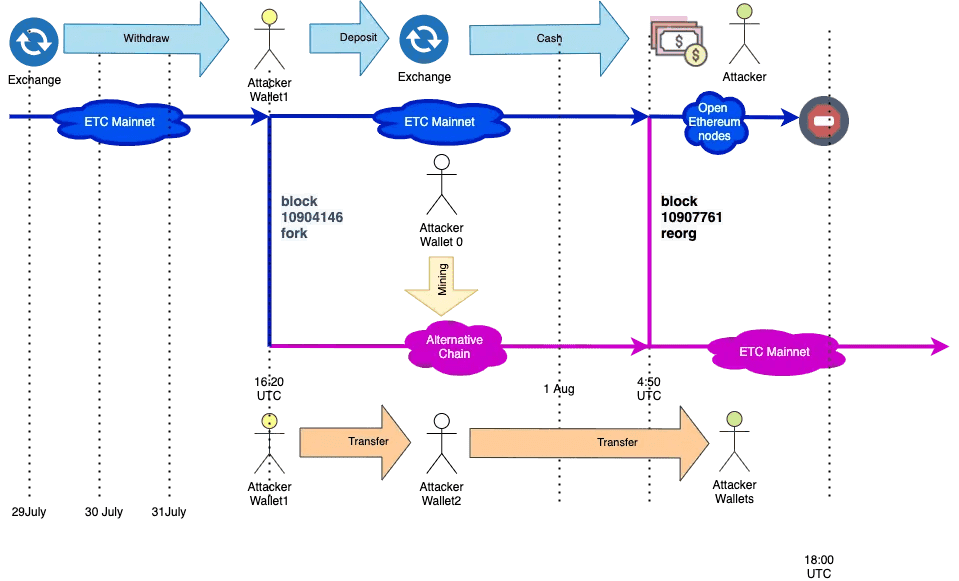
Ethereum Classic (ETC): This smaller sibling of Ethereum (using PoW) experienced multiple 51% attacks in 2019 and 2020. Attackers were able to reorganize the chain and double-spend, causing losses to exchanges. ETC’s hash rate was low enough that attackers could rent mining power (through services like NiceHash) relatively cheaply to outmine the network for short periods.
-
Bitcoin Gold (BTG): A Bitcoin offshoot, BTG was 51% attacked in 2018 and again in 2020. Attackers double-spent BTG, exploiting the network’s lower hash rate (BTG used a different mining algorithm than Bitcoin, but it wasn’t as secure due to less participation).
-
Other altcoins: Dozens of lesser-known PoW coins have been victims of such attacks when their mining power was low. In fact, any PoW coin is theoretically vulnerable if it’s not costly enough to acquire majority hash power. Some communities have responded by changing their mining algorithms or moving to Proof-of-Stake (as these attacks are mostly a Proof-of-Work issue).
These examples highlight that 51% attacks are a real threat for small networks. Attackers can even use cloud mining or rental services to avoid buying hardware – for instance, renting hash power for a few hours to overpower a weak network and profit from double spends. For Bitcoin, however, renting enough hash power is impossible – there isn’t enough available for hire to come close to Bitcoin’s level. According to some estimates, maintaining a 51% attack on Bitcoin could cost on the order of several million dollars per hour in electricity and rental fees, which is prohibitively expensive. In contrast, attacking a smaller coin might cost just a few thousand dollars.
Ethereum Classic 51% Attack (source)
Why a 51% Attack on Bitcoin is Unlikely (in 2025)
Several key factors contribute to Bitcoin’s resilience against 51% attacks as of 2025:
-
Enormous Hash Rate: Bitcoin’s hash rate has hit all-time highs in 2025. The network’s computing power has grown as mining technology advanced (more efficient ASICs) and more miners joined. Higher hash rate means more security – an attacker’s required resources grow in tandem. Bitcoin’s network is orders of magnitude larger than any other Proof-of-Work crypto, making it a very secure target. Any entity trying to amass such hash power would stand out and face many hurdles.
-
Decentralized Mining Ecosystem: Mining is more decentralized than it may appear from pool statistics. Yes, a few pools aggregate a lot of hash power, but pools are not single miners – they are groups. If a pool operator tried to abuse the pool’s hash power for an attack, miners in the pool would likely notice odd behavior (like withheld blocks or unusual payout issues) and could quickly abandon the pool. Pool participants can switch pools within minutes if needed. This acts as a check against any pool operator going rogue. The incentives for pool operators are also against attacking – they make steady fees from honest mining; an attack could destroy their business.
-
Economic Incentives: Bitcoin miners typically have heavy investments in equipment and earn in Bitcoin. Launching a 51% attack would directly harm the value of Bitcoin (if successful double-spends occur, trust in the network drops, price likely plunges). The attacker would be undermining their own investment. It’s often said that a rational miner gains more from continuing to mine honestly than from attacking, because the rewards of a healthy network outweigh short-term double-spend profits. The only scenarios where this might not hold are if the attacker’s motive isn’t profit (e.g., a malicious actor or competitor wanting to damage Bitcoin regardless of cost). But even then, they face the massive technical barriers described earlier.
-
Community and Developer Vigilance: The Bitcoin community is very alert to any signs of centralization. As seen in the past, if any single entity were to approach a majority of hash power, pressure and solutions emerge. Developers have considered ideas like detection systems for long block reorgs or ultimately changing the proof-of-work algorithm if absolutely necessary to thwart an entrenched attacker (though such a change would be contentious and last resort). Essentially, Bitcoin is not a static target – it’s an active ecosystem of users and engineers who would respond to existential threats.
-
Alternate Protections: While proof-of-work is about brute forcing hashes, Bitcoin’s design has some built-in protections against deep rewrites. For example, Bitcoin nodes by default won’t reorg back beyond 100 blocks, even if a longer chain appears, as a sanity check. Moreover, block finality increases with depth – an attacker would likely only manage to reverse a few blocks at most, because trying a reorg of hundreds of blocks would give everyone time to react or simply be rejected as implausible by the network at large. So, any realistic attack is limited in scope of what it can change.
-
The Cost Factor: Let’s put some rough numbers to it. Assume an attacker wanted to sustain a 51% attack for 1 hour. Bitcoin’s network might consume on the order of 130 terawatt-hours per year (this is a ballpark figure for the mid-2020s). That’s about 15 gigawatts on average. Half of that for one hour is 7.5 GWh of energy. Even at a low industrial electric rate (say $0.05 per kWh), one hour of half the network’s energy is $375,000 in electricity alone. Now add the fact they’d need to have hardware capable of delivering that power – if they rented it (impossible at that scale, but hypothetically), rental rates plus pool fees etc. would multiply costs further. Some estimates put the upfront cost of hardware in the billions of dollars and operational costs in the millions per day to sustain an attack on Bitcoin. All this for the chance to maybe double-spend some Bitcoins worth far less than what’s being spent on the attack – it’s economically irrational.
Beyond 51% Attacks: Other Security Considerations
The focus of “Can Bitcoin be hacked?” is usually on 51% attacks because that’s a known theoretical weakness of PoW blockchains. However, Bitcoin’s security also depends on other factors:
-
Software vulnerabilities: Could an attacker exploit a bug in Bitcoin’s code to create an attack that’s easier than 51%? The Bitcoin core software is open-source and heavily reviewed, but it’s software – bugs have existed. Notably, in 2018, a bug (CVE-2018-17144) was found that could have allowed an attacker to crash nodes or even inflate coins. It was fixed before being exploited. The community and developers work hard to catch and patch such issues. While not 51% related, a software bug is another angle someone might try to “hack” Bitcoin. Fortunately, none have resulted in a protocol-level catastrophe, and the network is very cautious with updates.
-
Quantum computing threat: Often people ask if quantum computers could hack Bitcoin. This is a different kind of threat – quantum computers in the future might break the cryptographic signatures (elliptic curve cryptography) that secure Bitcoin addresses, potentially allowing coin theft if Bitcoin doesn’t upgrade its algorithms in time. As of 2025, quantum computers are not near powerful enough to do this for Bitcoin’s cryptography. And the Bitcoin community is already researching quantum-resistant algorithms to potentially deploy years ahead of any practical threat. This is not a 51% attack, but it’s another angle on “hacking Bitcoin” often discussed. The bottom line: no immediate threat here, and likely plenty of time to adapt if it becomes real.
-
Social attacks and centralization: A 51% attack is a brute force method. But “hacking” Bitcoin could also mean influencing it in other ways – for example, if governments heavily regulate miners or if major mining operations collude on protocol changes. The true strength of Bitcoin is its decentralized consensus among users, nodes, and miners. Keeping a diversity of miners across different regions and stakeholders is key. The 2025 scenario of two pools briefly having ~51% combined was a centralization concern, but the community discourse and miners’ own incentives resolved it. It’s a reminder that the human element (governance, economic game theory) is as important as pure hash power numbers.
Risks of 51% Attack (source)
Conclusion: Bitcoin’s Security in 2025
Bitcoin’s blockchain has proven remarkably secure over the years. A 51% attack remains a theoretical threat rather than anything we’ve seen in practice with Bitcoin. The enormity of the network’s hash rate and the aligned incentives of participants make such an attack highly unlikely with current technology and economic conditions. Can Bitcoin be hacked via 51% attack? In theory yes, but practically no – not without enormous resources and self-defeating consequences for the attacker.
For everyday users and investors, the phrase “Bitcoin can’t be hacked” holds true in the sense that its cryptography and network consensus have held strong. When you make a Bitcoin transaction and it has several confirmations, you can be extremely confident it’s permanent. The chance of a malicious reorg of the chain (51% attack) is so remote, especially as confirmations grow, that it’s negligible for all but the largest transfers (and even then, risk is more about exchange security or user error than the chain itself).
That said, the Bitcoin community remains vigilant. The lesson from smaller coins is that vigilance is needed to maintain decentralization. The mining ecosystem continues to add new participants, and efforts are ongoing to ensure no single point of failure. It’s also why many enthusiasts support home mining or at least distribution of hash power globally, to avoid too much coming under one roof.
In conclusion, Bitcoin has never been successfully 51% attacked and is extremely well-fortified against such an event. As of 2025, it stands as one of the most secure computing networks on the planet. While no system is 100% invincible, any actor attempting to “hack” Bitcoin via a majority attack would face prohibitive costs and resistance. Bitcoin’s design, bolstered by over a decade of growth, ensures that it remains trustworthy and secure for users. Rest easy knowing that the network is doing its job, and focus on securing other aspects (like your personal wallets and keys) which are far more likely to be points of compromise than the blockchain itself.