Blockchain is touted as the most revolutionary technology to hit the financial services industry, banking the unbanked and returning power to the people. However, while Bitcoin was created to overthrow the existing centralized system, traditional finance and blockchain have a lot more in common than you’d think.
A cryptocurrency wallet relies on a key pair: a private key and a public key. The private key is a secret number that allows you to spend your crypto, while the public key (from which your wallet address is derived) can be shared freely to receive funds. Keeping your private key safe is paramount – anyone with it can access your coins, and if you lose it, you lose access yourself.
Understanding the difference between a public key and a private key is fundamental to grasping how Bitcoin and other cryptocurrencies work. These keys are the bedrock of cryptographic security in blockchain systems, serving as your digital identity and authorization mechanism. In this article, we’ll break down what public and private keys are, how they relate to wallet addresses, and why securing your private key is absolutely crucial (with real-world examples of what can happen if you don’t). We’ll also touch on how advances up to 2025, such as improved wallet technology and concerns like quantum computing, fit into the public/private key picture.
The Bitcoin Wallet Address
Just like banks use account numbers to keep track of everyone’s account balances, blockchain networks use wallet addresses. Bitcoin addresses are represented by an alphanumeric string of between 26 and 35 characters, usually beginning with 1, 3, or bc1. These addresses represent payment destinations, and while they are part of your public key, they aren’t the same thing.
To understand the difference between an address and a public key, it’s essential to know what a hash is.
What is Hash?
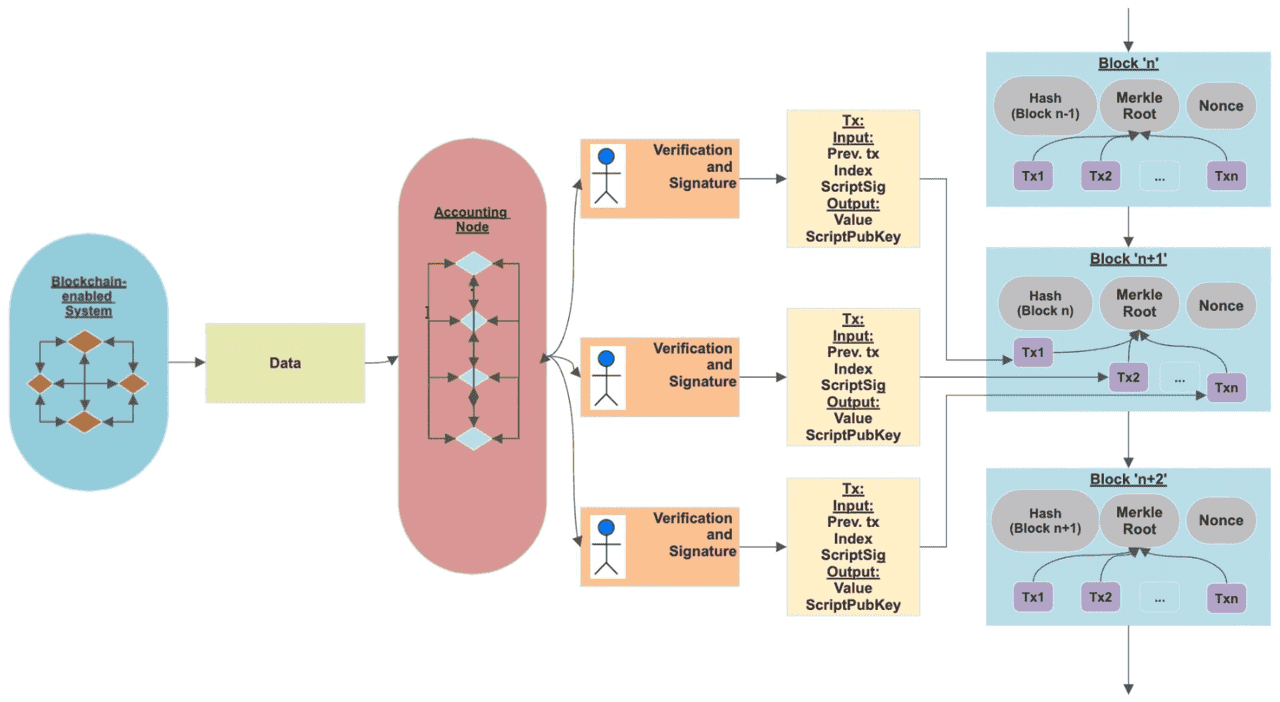
A hash function returns a value of specified length regardless of the input seed, and while it’s easy to create a hash, it’s near impossible to generate the original seed phrase.
Bitcoin uses a hash in addition to the public key for security reasons. If, for example, a vulnerability in the mathematic function used to generate keys was found that allowed people to derive a private key from a public key, your money would still be safe as your public key isn’t exposed until you make a transaction. Read Bitcoin Hash Rate to learn more.
Public Keys, Private Keys, and Addresses: The Basics
In Bitcoin (and many other cryptos), transactions are secured by public-key cryptography. That means each user has a public key and a private key that are mathematically linked. Here’s a simple analogy:
-
Think of your public key as your bank account number or email address – it’s something you can share with others so they know where to send you money or messages. In Bitcoin, your public key is often represented (after some processing) as a wallet address (the string of letters/numbers you share to receive BTC). For example, a Bitcoin address might look like 1BoatSLRHtKNngkdXEeobR76b53LETtpyT. This address is derived from your public key (more on that soon) and can be freely distributed. People use your address (public key) to send Bitcoin to you. The public key’s role is to receive funds and to let others verify signatures made by your private key.
-
Think of your private key as the PIN code or password to that account – it’s secret and grants control. The private key is a very large random number that, through cryptographic algorithms, allows you to prove ownership of the coins in the corresponding address. In Bitcoin, a private key is typically a 256-bit number (which can be represented as a 64-character hexadecimal string). Possession of the private key means you have the authority to spend the bitcoins associated with its public key. Never share your private key. If someone obtains it, they can access and spend your funds. Conversely, if you lose it, you lose access to your funds forever because nobody (not even a bank or Satoshi Nakamoto) can recover it for you.
To summarize: Public key = receive-only (shareable), Private key = spend/control (keep secret). Together, they enable the core Bitcoin functionality: you can receive money at your address, and later use your private key to authorize sending that money elsewhere.
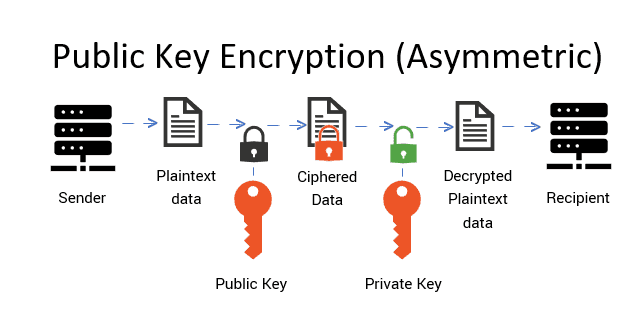
Public vs Private Key Asymmetric Encryption (source)
How Are Public and Private Keys Related?
A private key and public key are a key pair generated as part of public-key cryptography (specifically, Bitcoin uses the Elliptic Curve Digital Signature Algorithm, ECDSA). The relationship is such that the public key is mathematically derived from the private key. However, the process only works one way: private key -> public key -> address, but you cannot feasibly reverse it (i.e., you can’t deduce the private key from the public key or address, assuming standard cryptographic assumptions hold true).
When you later want to spend those BTC, your wallet will present the public key and a digital signature (created using your private key) to the network. Nodes can verify that the signature is valid for the public key and that the public key’s hash matches the address that has the coins. This cryptographic dance proves you own the private key without ever revealing the private key. The signature can only be made by you (with the private key), but it’s publicly verifiable with your public key.
This is why keeping the private key secure is everything – it’s the secret that allows the creation of valid signatures. And it’s why you can safely share your address (derived from the public key) with anyone – it’s impossible for them to “reverse engineer” your private key from it under current technology.
Bitcoin Privacy and Publicity
The number of terms used to describe a Bitcoin transaction’s elements can be overwhelming, especially when there are many different forms of the same thing. For example, public keys are generated using co-ordinates on an elliptic curve, which implies knowing one co-ordinate is enough to derive the second co-ordinate. This means the X co-ordinate alone can represent the public key, producing what is called a ‘compressed public key.’
This can be hard to distinguish as the hash of the compressed and uncompressed public keys give different addresses of the same length. Some speculate that Satoshi, the anonymous creator of Bitcoin, did not know about public key compression before departing from the project’s development and used hashing to create more compact identifiers.
Addresses are indeed shorter than public keys, but they also bring protection against various cryptographic attack vectors. They include features that aren’t available with just a public key, such as a built-in checksum for every address, allowing systems to detect when someone mistypes a character before sending their funds into oblivion.
However, while addresses and keys are simple once you’ve understood them, they aren’t as easy to remember as, say, an Instagram username. This has led many efforts into creating addresses that are as secure as Bitcoin’s public key hash and as easy to remember as a website name.
For example, the Ethereum Naming Service allows users to tie their accounts to a personalized ‘.eth’ address, allowing people to send and receive any ERC-20 or other Ethereum-compatible token from a single address.
Private keys are generated using a pneumonic phrase – a set of words that act as a seed to the function that generates the private key. This seed phrase is generally a list of 12 to 24 randomly generated words used to recover all information regarding a wallet. The private key generation function takes five inputs, including a password, the number of iterations, salt, key length, and a pseudorandom function.
The password is the pneumonic phrase, and the function returns a private key from which both your public key and payment addresses can be derived. 256-bit private keys have 16^64 combinations, a fair bit more than the number of seconds in the average human’s life. Bitcoin’s SHA-256 encryption algorithm makes it next to impossible to guess a private key, even if the attacker already has a wallet’s address and public key.
Theoretically, Bitcoin can still be taken over by a 51% attack, and with quantum decryption techniques, the network’s security might need an upgrade in the years to come. However, as the Bitcoin network grows, controlling 51% of the network becomes increasingly difficult, and today even the largest mining pools don’t come close to maintaining anywhere near half the network. Bitcoin is only as secure as it is decentralized, and as a function of its network participation, the security of decentralized networks should improve with adoption.
Encryption General Overview (source)
The Importance of Keeping Your Private Key Safe
Your private key is essential for securing your cryptocurrency. Here are ways to protect it:
-
Use Trusted Wallets: Choose reputable wallet software or hardware wallets (like Ledger or Trezor) to safeguard your keys. Avoid random apps that might steal your key. Hardware wallets keep the key secure in a chip and minimize risks from malware.
-
Backup Your Keys/Seed: Write down your seed phrase (12/24 words) and store it securely, not just digitally on your devices. Consider engraving it in metal for durability. A lost device without a backup means lost crypto, so keep this backup secret.
-
Strong Encryption for Digital Backups: If you must store backups digitally, use strong encryption (e.g., VeraCrypt). However, remember your passphrase – forgetting it could lock you out.
-
Multi-Signature for Large Holdings: For significant amounts, consider a multi-sig wallet where multiple keys are needed for transactions. This enhances security and ensures you don’t lose access if one key is lost.
-
Cold Storage: Keep your private keys offline using a paper wallet or a hardware wallet. Long-term holders should store most of their crypto in cold storage to avoid online threats.
-
Beware of Scams: Be cautious - no legitimate service will ask for your private key. If someone requests it, that's a red flag. Once stolen, crypto cannot usually be recovered.
Stay vigilant and treat your keys as the treasure they are.
Things to Address
Despite all its security measures, Bitcoin’s encryption algorithm could be rendered obsolete by a new form of computing. Quantum computers can perform calculations that take traditional computers decades or even centuries in mere minutes. According to experts, quantum computers could crack Bitcoin’s SHA-256 algorithm within just 30 minutes. In theory.
Is Bitcoin Safe?
Realistically, Bitcoin is perfectly safe, and even if quantum computers find an algorithm to crack encryption, quantum encryption algorithms will be quick to replace them. In fact, some modern security measures can combat quantum computing today – multi-sig wallets are used to store funds that a group of individuals controls.
What are multi-sig wallets?
Multi-sig wallet addresses start with a three and use a script to define the rules for creating a transaction, including how many signatures are needed for a transaction to go through. Transactions from multi-sig wallets need to be approved by a pre-determined number of signatures, sometimes all of the signatures involved. This means even if one address is compromised, it won’t take control over the wallet’s funds.
When you transfer cryptocurrencies to a wallet on an exchange, you could be risking those funds to attackers depending on that exchange’s security. It’s crucial to store your assets securely offline to keep your holdings as safe as possible from malicious users. There are a few ways to do this, ranging from the technologically sophisticated hardware wallets to a scribble of paper.
The most natural step from an online exchange wallet is to an offline software wallet. This usually involves downloading an application to your computer or smartphone, which will generate your private key and store your cryptocurrencies securely. It is recommended to use a separate computer or phone that remains disconnected from the internet since users have had varying levels of success by limiting the application’s access to the Internet through software.
However, most software wallet vulnerabilities are well documented and are still much more secure than using an exchange wallet online. To take things one step further, you can even store your private key seed phrase on a piece of paper and hide it somewhere safe. As long as you ensure no one else has access to this seed phrase, no one but you should have access to your funds. This is widely regarded as the safest and most inexpensive way to store your cryptocurrencies.
How to Keep Your Bitcoin Safe?
The most convenient and expensive option of the bunch is the hardware wallet. These are physical devices used to store private keys but have a lot of built-in functions that can make storing crypto offline a little less cumbersome.
For one, a single hardware wallet can store multiple cryptocurrencies and can even be connected to the internet via USB to transfer funds to and from an exchange. Some hardware wallets even come with multi-sig capabilities and use LCD screens to present information even when not connected to a computer.
Blockchain Quantum Resistance (source)
Are Bitcoin Keys Quantum-Proof?
A key concern in the crypto community is quantum computing. Quantum computers could potentially solve problems that underpin public key cryptography, which may allow them to derive private keys from public ones, posing a risk to systems like Bitcoin. However, as of 2025, quantum computers are not advanced enough to break Bitcoin’s cryptography. Experts estimate it may take a decade or more for this to become feasible.
The community is proactive, with researchers and institutions like NIST developing quantum-resistant algorithms. In 2024, NIST finalized new encryption standards, and Bitcoin could transition to quantum-resistant signature schemes if necessary, likely through a soft fork.
Currently, not reusing addresses can provide some protection against quantum attacks since public keys from unused addresses remain unknown to attackers. Multi-sig and other security measures could also enhance protection, though a powerful quantum computer might still compromise them.
If Bitcoin’s cryptography were suddenly at risk, it would have significant implications for digital security overall. However, the Bitcoin community is aware of the potential threat and is actively exploring solutions. For now, Bitcoin is considered safe from quantum attacks, with ongoing research into countermeasures and post-quantum algorithms.
Conclusion
Public and private keys are the heart of the Bitcoin revolution – they enable trustless transactions, meaning you don’t have to trust a middleman, just the math. Your public key (and its handy form, the address) is your public identity on the blockchain, allowing others to send you value. Your private key is your secret that unlocks that value and proves your ownership. This elegant system provides both security and freedom: no one can spend your Bitcoin without your private key, and conversely, with your private key you don’t need anyone’s permission to transact.
As of 2025, the usage of public/private keys has expanded beyond just cryptocurrency wallets. They’re used in decentralized identity solutions, authentication mechanisms, and more. But the core principle remains: protect your private keys like your financial life depends on it – because it does in the crypto world. Unlike a bank account password which, if stolen, you might reset by calling the bank, a stolen crypto private key has no reset button and stolen funds typically cannot be recovered. This is the trade-off of the power crypto gives you.
On the positive side, if you follow good practices, your crypto can be extremely secure – far more secure from theft or censorship than money in a traditional system. There’s no bank that can fail or freeze your account, no centralized database hackers can breach to get your info (hackers instead target individuals, which is why your personal vigilance is key).