When it comes to crypto trading, nothing is more important than the safety of your assets. Every investor, regardless of skill and experience, wants to know that their coins are secure even when the market is volatile. At Phemex, asset protection rests at the foundation of everything we build.
Through a combination of cold-warm-hot wallet infrastructure, multi-signature authorization, advanced encryption, and 24/7 wallet monitoring, Phemex has created one of the most secure asset-storage systems in the exchange industry. Let’s explore how each component works together to keep your crypto safe, efficient, and always within reach.
Why Asset Security Defines Trust in Crypto
Security breaches remain one of the biggest risks in the digital-asset ecosystem. Exchange hacks, insider threats, and private key leaks have caused billions in losses over the past decade. Traders today need not only high-performance platforms but also bulletproof custody systems that safeguard funds against every imaginable threat. Phemex’s mission goes beyond providing a fast and user-friendly trading experience. Our goal is to create a fortress-grade infrastructure in which advanced cryptography, monitoring mechanisms, and strict operational controls work in harmony to protect every cent you deposit.
Cold-Warm-Hot Wallet System: Layered Protection by Design
At the heart of our asset-security model is a three-tier wallet architecture that was purposely constructed to balance maximum safety with seamless liquidity.
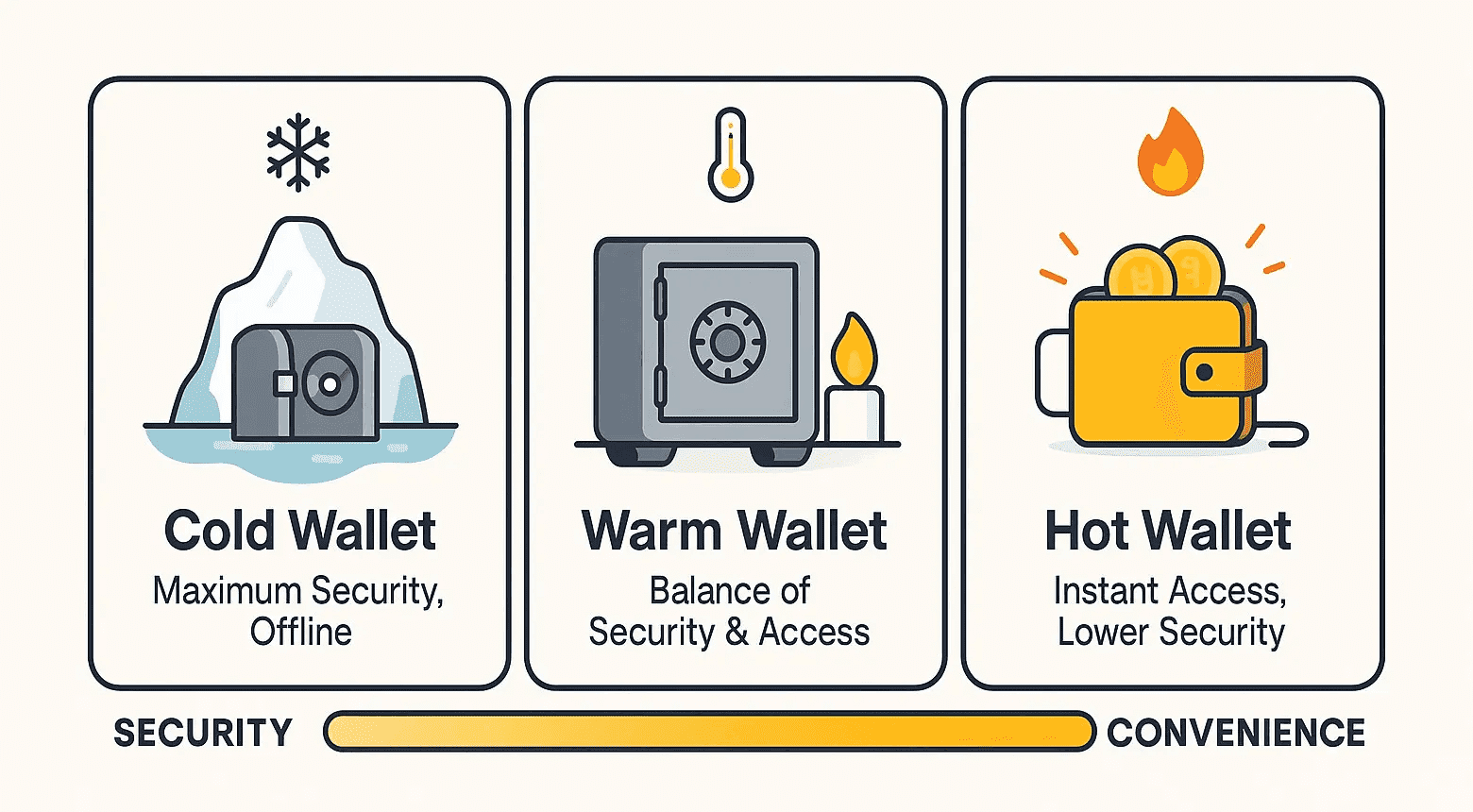
Cold vs Warm vs Hot Wallets (source)
-
Cold Wallets (70%+ of total assets)
Cold wallets are completely offline so they remain disconnected from the internet and isolated from potential external threats. The majority of all user assets on Phemex (over 70%) are stored in these wallets, ensuring they remain immune to hacking attempts or network-based intrusions.
Each cold wallet is maintained in multi-signature custody which requires multiple authorized personnel to approve any transfer. Transactions from cold storage are processed manually after multiple verifications to minimize any possibility of unauthorized movement.
-
Warm Wallets (~20% of total assets)
Warm wallets serve as a secure bridge between cold and hot wallets. They store a limited portion of assets in order to provide operational flexibility for liquidity management and withdrawals without directly exposing funds to the internet.
By maintaining this buffer, Phemex can execute large withdrawals or process market-driven liquidity demands quickly while keeping cold assets untouched. It’s a harmonious balance of safety and efficiency.
-
Hot Wallets (<8% of total assets)
Hot wallets handle real-time user operations, including deposits, withdrawals, and transfers. These wallets are online and optimized for speed, but Phemex enforces strict access controls and advanced encryption to protect private keys.
Only a small fraction (less than 8%) of total assets ever reside in our hot wallets at any given moment, which is a deliberate design choice that minimizes exposure while ensuring a smooth trading experience.
By distributing funds across cold, warm, and hot layers, we ensure that even if a single system is compromised, your funds remain protected. Cold storage is safe but slow, while hot wallets are fast but exposed. By using warm wallets as an intermediate layer and real-time monitoring to manage liquidity, we maintain the operational agility users expect (deposits are processed instantly, withdrawals remain swift) without ever compromising safety. This multi-tiered model is the gold standard in exchange security architecture.
Multi-Signature Security: No Single Point of Failure
Crypto security often depends on how private keys are managed. A single key in the wrong hands can mean immense disaster. Phemex eliminates this vulnerability with multi-signature (multi-sig) authorization.
How it works:
-
Each high-value transaction requires multiple independent approvals from authorized team members.
-
Each signer holds a unique portion of the cryptographic key, and only when all pieces are combined can a transaction be executed.
-
No single individual, not even a system administrator, can access or move funds alone.
This distributed-key model prevents insider threats, phishing attacks on staff, or rogue actions by a compromised account. It’s a collaborative security system built on checks and balances. In addition, our internal processes ensure that signers are located in different physical and network environments so that coordinated breaches are virtually impossible.
Advanced Encryption: Protecting Keys with Modern Cryptography
Phemex leverages state-of-the-art encryption technologies to protect private keys and wallet data from every conceivable attack vector.
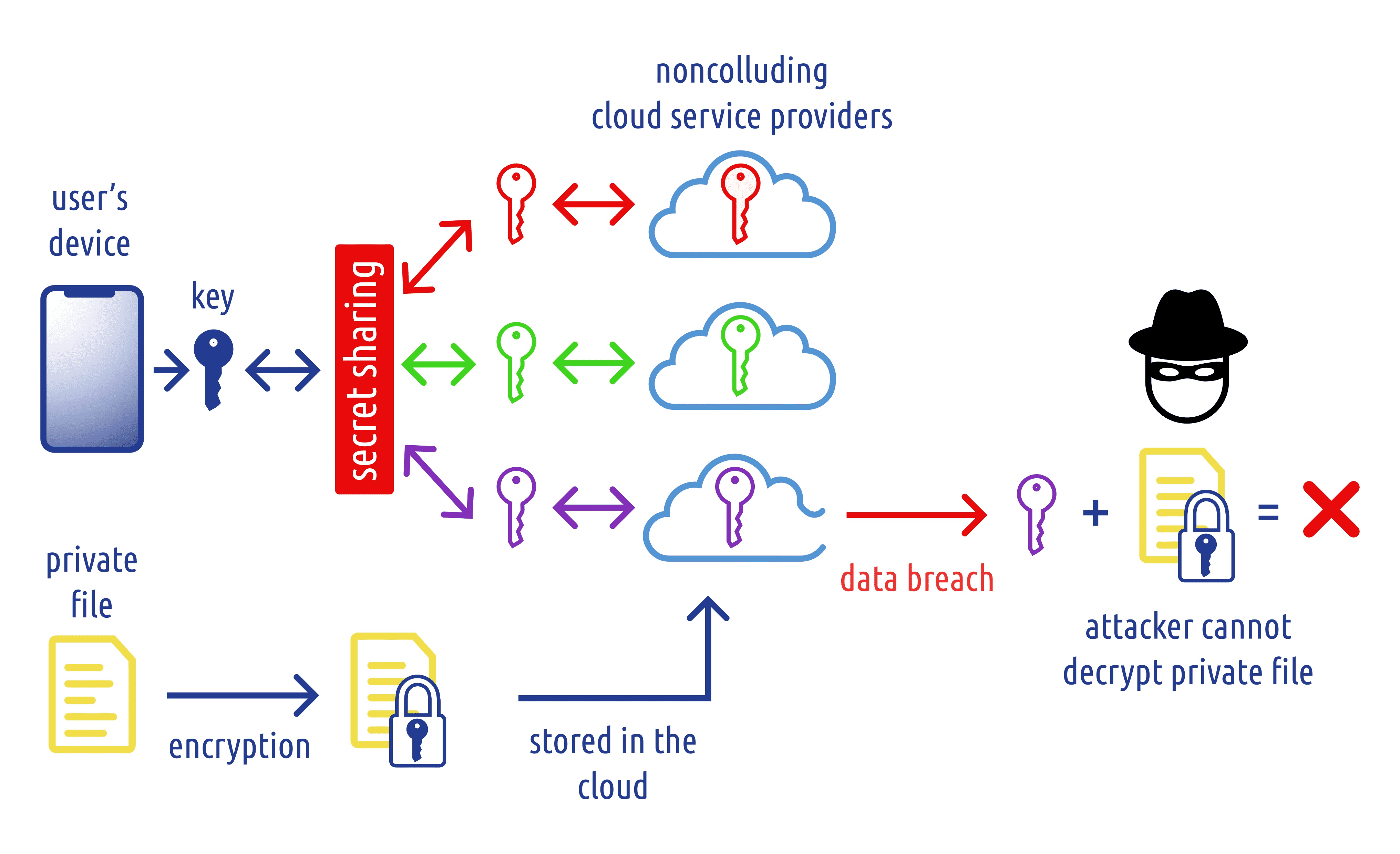
Shamir Secret Sharing (source)
Shamir Secret Sharing
Private keys for hot wallets are split into multiple encrypted fragments using Shamir Secret Sharing, a proven cryptographic technique that divides a secret into several parts. A predefined threshold of these parts is required to reconstruct the original key. This means no single server, database, or employee ever holds full control. Even if one fragment were somehow compromised, it would be mathematically useless without the rest.
AWS Nitro Enclave Technology
These encrypted fragments are stored and processed in AWS Nitro Enclaves, which are isolated computing environments that prevent administrative access, external connectivity, or unauthorized data extraction. Nitro Enclaves enable key management operations such as signing withdrawals to occur in sealed, hardware-verified environments. Administrators can’t peek inside to intercept or interfere with data.
Together, Shamir Secret Sharing and Nitro Enclave create a next-generation key-protection framework where sensitive cryptographic operations remain fully isolated and verifiable.
24/7 Wallet Monitoring
Phemex doesn’t just hold your assets, we also watch over them around the clock. Our automated monitoring systems continuously analyze all wallet activity across cold, warm, and hot layers to detect anomalies in real time.
The system evaluates:
-
Transaction frequency and size
-
Recipient addresses
-
Network latency or connection irregularities
-
Behavioral deviations from historical patterns
When anything unusual is detected, the transaction is paused and flagged for manual review by the security team. This combination of detection and human oversight provides a dual-layer safety net that’s fast enough to catch anomalies instantly, yet meticulous enough to allow legitimate transactions to continue unhindered.
Conclusion
By integrating advanced cryptography, distributed control, and continuous monitoring, Phemex has engineered one of the most resilient security architectures in the crypto world. Every wallet, every transaction, every private key is shielded by multiple defenses that evolve alongside emerging threats. In the crypto industry which is built on innovation, security remains the true measure of reliability. On that front, Phemex stands firm in safeguarding your assets so you can trade, invest, and grow with complete confidence.
Want to learn more about how we keep you safe?