In the world of cryptocurrency, platform security is the invisible shield that protects everything users do - from logging in to executing a trade to withdrawing hard-earned funds. While most are aware of visible safeguards like two-factor authentication or withdrawal whitelists, the deepest layer of protection often happens behind the scenes.
At Phemex, our security architecture extends far beyond account and asset protection. It encompasses network defense, firewalls, DDoS mitigation, web and application security, and a 24/7 security operations center that never sleeps. Together, these systems form a resilient, multi-layered fortress to guarantee a safe, stable, and uninterrupted trading experience for the Phemex community.
Why Platform Security Matters in Crypto
Cryptocurrency exchanges are among the most targeted platforms in the digital world. Cybercriminals constantly probe trading systems, APIs, and servers looking for vulnerabilities they can exploit. A single breach can lead to data leaks, service interruptions, or even large-scale financial theft.
Phemex takes a defense-in-depth approach that combines enterprise-grade infrastructure with real-time threat detection and expert human oversight. We believe that security must be proactive, not reactive. Every packet, request, and transaction that passes through our platform is protected by multiple layers of intelligence-driven defense.
Network and Firewall Protection: The First Line of Defense
The foundation of Phemex’s platform security is our network protection framework that’s powered by cybersecurity industry leader Palo Alto Networks’ enterprise firewalls.
These firewalls meticulously inspect all traffic entering and leaving the Phemex system and filter out malicious requests and unauthorized access attempts. They don’t only block known threats, but also use deep packet inspection (DPI) and machine learning to identify new, emerging attack patterns in real time.
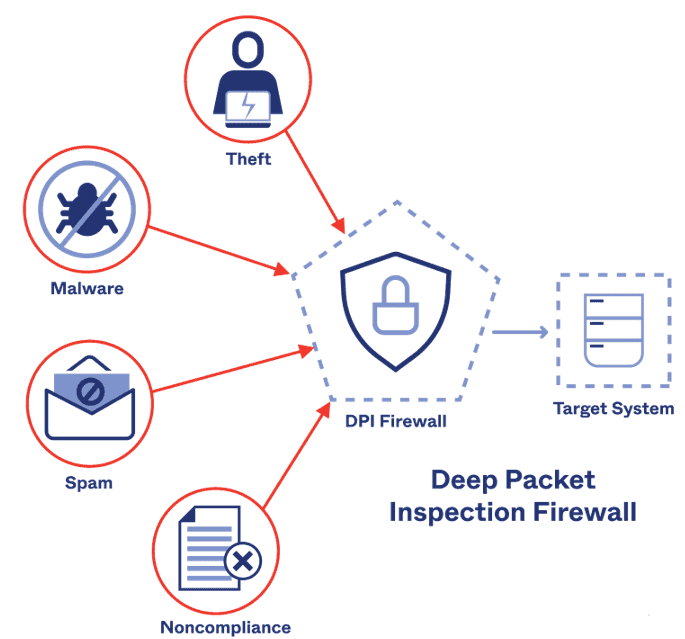
Deep Packet Inspection (source)
Network Segmentation
To further reduce risk, Phemex employs network segmentation which divides our infrastructure into isolated zones. This means that even in the unlikely event of a compromise, attackers cannot move laterally from one system to another.
For example:
-
Trading engines are separated from web servers.
-
Wallet management systems are isolated from public-facing APIs.
-
Internal admin networks are completely inaccessible from the internet.
This segmented design creates multiple layers of containment to make sure that sensitive components of the Phemex ecosystem remain protected, even if another layer were somehow exposed.
DDoS Defense: Always Online and Stable
Distributed Denial of Service (DDoS) attacks are among the most common and disruptive threats to online exchanges. By overwhelming servers with junk traffic, attackers can attempt to take platforms offline or slow down user operations.
Here at Phemex, uptime isn’t negotiable. We’ve deployed a globally distributed DDoS defense network that’s capable of identifying and neutralizing these attacks automatically without affecting normal users.
Components:
-
Traffic Filtering: Incoming traffic is continuously analyzed at edge servers worldwide. Malicious requests are filtered out before they ever reach the core infrastructure.
-
Anomaly Detection: Advanced algorithms detect abnormal traffic spikes or suspicious IP patterns in real time.
-
Mitigation and Scaling: When an attack is detected, the network instantly scales bandwidth capacity and reroutes traffic through protective layers to absorb and neutralize the threat.
This combination of automation, distribution, and resilience allows Phemex to maintain near-100% uptime, even during high-intensity DDoS events that could cripple lesser exchanges.
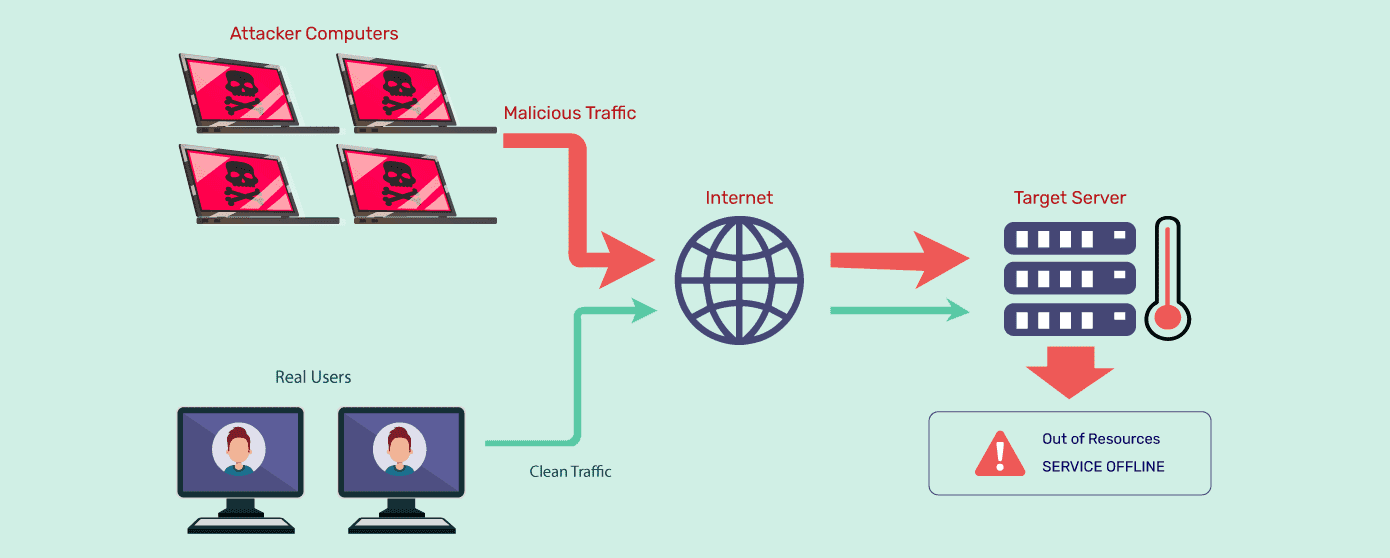
DDoS Attack (source)
Web and Application Security: Fortifying the User Experience
While network protection guards the perimeter, Phemex’s web and application security framework secures everything users interact with - from login portals to APIs and trading dashboards.
Web Application Firewall (WAF)
Our Web Application Firewall acts as a smart filter for all web requests and block common exploit attempts such as:
-
SQL Injection (SQLi): Preventing attackers from manipulating database queries.
-
Cross-Site Scripting (XSS): Stopping malicious scripts from hijacking sessions or stealing data.
-
Cross-Site Request Forgery (CSRF): Ensuring that all transactions are initiated by legitimate, verified users.
The WAF is continuously updated with new threat signatures in order to protect Phemex from both known and zero-day exploits.
Rate Limiting and Bot Detection
To maintain performance and integrity, we also implement rate limiting and bot detection mechanisms. These systems ensure that legitimate users and trading bots operate smoothly, while malicious or abusive requests are throttled or blocked. Combined with input validation and API request verification, these protections ensure that no unauthorized or malformed data can interfere with trading operations.
24/7 Security Operations: The Human Intelligence Layer
Even the most advanced systems need expert human oversight. Phemex operates a 24/7 Security Operations Center (SOC) that consists of a dedicated team of analysts, engineers, and responders who monitor every corner of the infrastructure.
The SOC uses Splunk Security Information and Event Management (SIEM), one of the industry’s most powerful monitoring and analytics platforms, to aggregate and analyze logs from every system in real time. Every event from API requests to firewall alerts is tracked and correlated using Splunk’s AI-powered analytics engine. When an anomaly or potential intrusion is detected, the SOC immediately initiates a response using automated playbooks or manual investigation depending on severity.
Conclusion
Platform security is the heartbeat of Phemex’s reliability. It’s what allows traders to execute millions of transactions daily without worry, knowing that behind every click stands a fortified fortress of technology and expertise. From firewalls and DDoS defense to WAFs and 24/7 monitoring, every component is designed to defend, detect, and respond. When you trade on Phemex, you’re relying on one of the most secure infrastructures in the crypto industry.
Want to learn more about how we keep you safe?