Cryptocurrency has many different aspects, not just coins and tokens. The technology surrounding crypto is continuously evolving, becoming faster, more secure, less polluting, and more private or anonymous. CryptoNight is a part of that. Considered one of the most common hashing or mining algorithms, it was created in response to two issues: a lack of privacy in transactions on the blockchain and increasing centralization from dedicated ASIC mining hardware.
What Is CryptoNight?
CryptoNight is a hashing algorithm that was developed in 2013 to support the CryptoNote protocol. It runs on CryptoNote’s Proof-of-Work (PoW) consensus, meaning that miners must solve complex mathematical equations to mine, and it was created for two reasons:
- To enable untraceable transactions:Despite Bitcoin (BTC) being initially deemed as “untraceable currency,” in many ways the opposite is true. Thus, where BTC transactions are publicly displayed on the blockchain (easily viewable if one knows the public address), CryptoNight aimed to add privacy to individual transactions.
- To curb the mining dominance of Application-Specific Integrated Circuits (ASICs):The rise of ASICs has meant individuals have no chance to compete in cryptocurrency mining. This has led to an unequal mining community and a threat of centralization to blockchains and cryptocurrencies. CryptoNight aims to put a stop to this and thus restore equality.

How Does CryptoNight Enable Untraceable Transactions?
To address the privacy concerns for cryptocurrency users, CryptoNight was designed with two important privacy technologies:
- Ring Signatures: This consists of creating a ring of possible signers, including the actual signer and other non-signers, who are all valid and equal, to authorize a transaction. Their signatures are all merged, rendering it impossible to know who the true signer is.
- Stealth Address: Stealth addresses provide additional security to the recipient of a transaction. The system requires the sender of a digital currency to create a random one-time address for a given transaction. This means that multiple transactions can be masked as having come from different one-time addresses, which makes them harder to trace.
These features achieved their goal but also led to the delisting of various privacy coins from popular cryptocurrency exchanges (DEXs and CEXs) due to regulatory concerns.
What Are the Different Types of Mining?
To fully understand why CryptoNight was developed and why it aims to combat ASIC mining, it is important to first understand what types of mining there are. In the early days of cryptocurrency, all Bitcoin (BTC) mining was carried out on individual home computers using CPUs, meaning that the opportunities were shared.
However, as crypto became increasingly lucrative and competitive, units with faster computations, and thus higher ability to earn rewards, came to dominate the market. This meant that slower or less powerful mining equipment could not compete, and unprofitable and finally obsolete. Those with more powerful and more expensive equipment soon pushed out competitors. With their rewards increasing, these mining companies bought more equipment and soon came to dominate mining, finally posing a threat to the decentralization of blockchain. There are four main types of equipment used for mining:
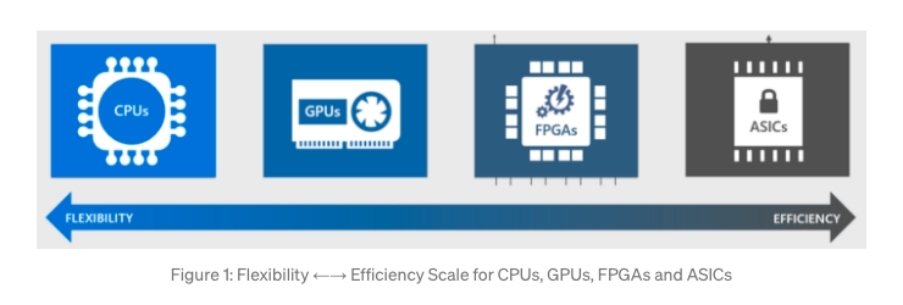
- Central Processing Units (CPUs):This is the simplest form of mining and can be carried out using a home computer or even a mobile phone. This makes mining more accessible to more people, but profits are low as they cannot compete with more powerful equipment.
- Graphics Processing Units (GPUs):This is the next step up from CPU mining and requires a graphics card. The initial costs and maintenance costs can be quite high, but it is more efficient and profitable than CPU mining.
- Application-Specific Integrated Circuits (ASICs):These circuits are specifically built for mining and can be very profitable. They require large amounts of energy and lots of space, especially since ASIC miners tend to have more than one. Unlike other types of mining devices, ASICs can only be used to mine cryptos and nothing else.
- Field Programmable Gate Arrays (FPGA):These are similar to ASICs, but can be reprogrammed to target certain algorithms, whereas ASICs are custom built to a particular algorithm. They are expensive but can also be very profitable. Despite not being as efficient as ASICs, their ability to be reprogrammed has made them a favorite with cloud mining.
Mining in cryptocurrency today requires huge processing power and money, not only for the computers themselves, but also the electricity, storage facilities, transportation, and so on. All of this has meant that mining is increasingly concentrated in the hands of the few who can afford it, which in turn has meant increasing centralization. CryptoNight aims to challenge this.
How Is CryptoNight Structured?
Despite using a PoW consensus, as does BTC’s SHA-256 algorithm, CryptoNight differentiates itself in its design to be more compatible with the CPUs of home PCs. This was specifically done to try and steer mining from the dominant ASICs, back to the people and thus re-decentralize mining. CryptoNight employs the following methods to achieve its purpose:
- Requiring random access memory (RAM):ASICs are traditionally built with a focus on hashing algorithms that do not need access to memory, such as the SHA-256 algorithm. They are only limited by how fast they can do the calculations. In order to make GPUs and CPUs competitive, CryptoNight requires access to memory per each mining instance. This favors CPUs and GPUs, which do have access to memory, and makes it difficult for ASICs.
- Latency dependency:Latency refers to the amount of time needed for a calculation to be issued, while the dependency refers to the fact that CryptoNight does not allow a second calculation to be carried out until the first is finished. CryptoNight’s reliance on RAM means that 2MB of memory is needed for each calculation, while its latency dependency means that creating a new block depends on all the previous blocks. This becomes very memory-intensive work, which is not suitable for ASICs.
- Designing a scratchpad that exactly fitsthe per-core L3 cache on Intel CPUs (about 2MB): Although CryptoNight allows for GPUs, it favors CPUs. To this end, the algorithm designed its working data to match the size of the shared cache memory per-core in a modern CPU. This type of memory is low latency when compared to GPUs and so CPUs have a significant advantage, which makes mining more equal.
How Has CryptoNight Evolved?
ASICs are continuously developed and custom-built to target specific algorithms. To that end, CryptoNight has had to continue evolving, something which it has done through tweaks and forking. The hashing algorithm went through many initial versions, as its original version, CryptoNight v0, was inefficient at stopping ASICs. Cryptocurrencies running on the algorithm, including Monero and Aeon, also made their own modifications and forked to try and reduce ASIC mining. Until now, however, no algorithm is 100% ASIC-proof. Some of the key CryptoNight versions are as follows:
- CryptoNight-Light was designed to use a smaller scratchpad, around 1MB, for easier hashing on lower-end hardware.
- CryptoNight-Heavy was implemented with a larger scratchpad, around 4MB, to see if being more memory-intensive could fend off ASICs.
- CryptoNight v7 was developed from the above variants, with the CPU targeted scratchpad size of 2MB. Upon new ASICs being found once more, it was further tweaked to become CryptoNight v8.
How Effective Is CryptoNight at Combating ASIC Mining?
It is impossible to completely stop ASICs, as the chips are custom manufactured and specifically designed for a particular hashing algorithm. Thus, it was soon established that to halt ASIC mining, algorithms needed to fork often. This would mean tweaking the mining algorithm and thus forcing a new ASIC to be custom built. CryptoNight v7 was built for this reason, after which CryptoNight v8 was established in October 2018.
By the end of December 2018, however, new ASICs had again been detected. This was particularly relevant when looking at Monero (XMR), when in February 2019, despite using CryptoNight to eliminate ASICs, the rigs were found to dominate its mining by over 85%. This meant that it was still impossible to be fully ASIC-resistant and so CryptoNight had failed. The finding also highlighted how ASIC mining was decreasing with each fork, only to return again after having the time to be redesigned. This meant that though impossible to eliminate entirely, ASIC domination could be continuously delayed, lending credence to the theory that forking would be the way forward for CryptoNight.
However, forking comes with its own problems, as with regular updates come some unwanted changes. For example, a fork in 2018 ended up creating three new currencies for Monero (XMO, XMC, XMZ) and de-anonymizing transactions. This was an issue, as many CryptoNight currencies, such as Bytecoin, could not allow this to happen – being that it is one of its founding principles. Thus, forking is not always an option, and CryptoNight has had to fluctuate between fighting ASICs and allowing ASICs, depending on the available technology at any given time.
What Coins Use the CryptoNight Hashing Algorithm?
CryptoNight, as the hashing algorithm designed by CryptoNote, already had its first coin in Bytecoin (BCN), which is CryptoNote’s coin. Following that, in 2014, prominent coin Monero joined the algorithm, and with that, more followed. Monero’s desire to be ASIC-free and CryptoNight’s failure on that point, however, finally led it to abandon the algorithm for RandomX. This did not spell the end for the algorithm though. With the different technology offered in the various versions of CryptoNight, coins have stayed and used the one that most fits their needs. Some opt for lesser ASIC-resistant versions, such as v0, while others choose the most robust at this point, such as v8. Additionally, as coins have forked, some have forked to other versions of CryptoNight, while others have adopted different algorithms altogether. The current list of CryptoNight coins includes B2B Coin, Balkancoin, Bold, and Bytecoin, among others.

Conclusion
CryptoNight is a robust algorithm that has brought some equality back to mining but has still never fully achieved its purpose of being ASIC-resistant. Its ability to give a higher level of anonymity to transactions and to mask the sending address offers an edge over some other algorithms and protocols. The fact that it works alongside its protocol CryptoNote and coin Bytecoin also offers enticing future possibilities, as it has all the necessary provisions to keep experimenting. Thus, as technology evolves, it is possible that CryptoNight will one day be able to fully realize its promise of being an equalizer for cryptocurrency mining.
Read More
- What are ASIC-Resistant Cryptocurrencies: A Brief Introduction
- What is Crypto Mining & How does it Work?
- What are Crypto Mining Rigs: An Overview of ASIC, GPU and CPU Miners
- Monero: The Invisible Network
- What Are Mining Pools: The Massive Cooperatives That Power Blockchain
- Crypto, Bitcoin, and the Power of Network Effects
- What is Cryptocurrency & How It Differs From Digital Cash
- What is Cryptocurrency & How does it Work?