In the digital currency space, data is as valuable as currency. When you trade, deposit, or verify your identity on a cryptocurrency exchange, you entrust that platform with your most sensitive information from identification documents and payment details to behavioral data and login credentials.
At Phemex, we treat this trust with immense care. Our philosophy is that your data belongs to you, and protecting it is one of our highest priorities. Through end-to-end encryption, strict access control, data isolation, regular audits, and regulatory compliance, we make sure your private information stays confidential and compliant with international standards.
Why Data Security and Privacy Matter
In the crypto space, data breaches can be just as damaging as financial hacks. A leaked private key, stolen ID document, or exposed email list can lead to identity theft, phishing scams, and reputational damage. That’s why data protection at Phemex goes far beyond traditional cybersecurity. Besides just securing transactions, we also secure every byte of information that flows through our systems. Whether it be login credentials, trading history, or KYC documents, your data is encrypted and accessible only to those who absolutely need it.
End-to-End Encryption
The cornerstone of data protection at Phemex is end-to-end encryption which makes your data unreadable to anyone except its intended recipient.
Encryption in Transit
Every piece of data moving between your device and Phemex servers is protected using Transport Layer Security (TLS 1.2 and above). This means that even if a malicious actor were to intercept network traffic, they would see only encrypted and indecipherable information.
Encryption at Rest
Once your data reaches Phemex servers, it remains protected through AES-256 encryption. This is one of the strongest standards used in global banking and military systems. All private keys, KYC documents, and user records are encrypted before being stored so that they remain secure even in the unlikely event of physical compromise.
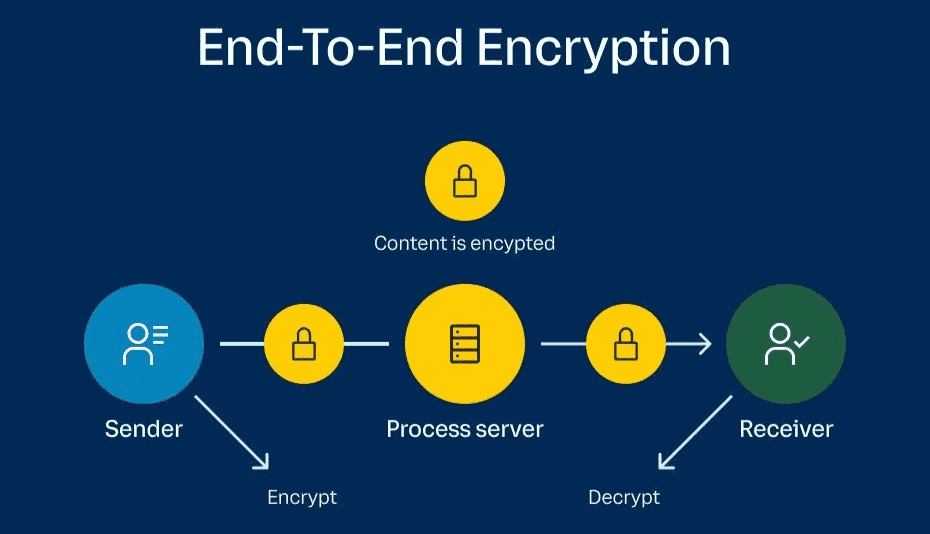
End-to-end encryption (source)
Key Management and Rotation
Phemex uses Key Management Systems (KMS) to handle cryptographic keys with strict control and rotation policies. Encryption keys are stored separately from the data they protect and are regularly rotated to prevent any potential misuse or correlation attacks. Access to decryption is strictly logged and audited, meaning every key-related operation leaves a verifiable record to reinforce transparency and accountability.
Strict Access Control
At Phemex, we believe that the fewer people who can access data, the safer it remains. Our role-based access control framework ensures that employees only have permission to view the information necessary for their specific responsibilities.
Role-Based Permissions
For example:
-
A customer support agent can verify account activity but cannot view withdrawal addresses.
-
A compliance officer can review KYC data but cannot access user login sessions.
Each system role is defined with precision, minimizing unnecessary privileges and drastically reducing the attack surface.
Privileged Account Monitoring
For higher-level administrative or engineering accounts, Phemex enforces additional layers of monitoring:
-
Privileged accounts must authenticate with multi-factor security.
-
Actions by these accounts are logged and reviewed.
-
Permissions are reviewed quarterly or whenever a role changes.
This creates a culture of trust and full accountability, as even internal operations are subject to the same strict scrutiny as external access attempts.
Data Isolation
Data security is not just about encryption but also about isolation. Phemex enforces logical separation of user data so that no account can access or influence another’s information.
Each user’s data resides within isolated logical environments in our databases. Even when queries are run for analytics or auditing, the system enforces query-level isolation. Each request can only access the specific dataset it’s authorized to retrieve. This design prevents cross-account access and eliminates the risk of data leakage between users, partners, or services. It’s the same architectural principle used by leading cloud providers and financial institutions worldwide.
Regular Audits and Encrypted Backups
Our security mechanism doesn’t stop at encryption and access control, as it also requires continuous verification and being ready for the unexpected.
Continuous Auditing
Every interaction with user data is automatically recorded in immutable audit logs. These logs capture:
-
Who accessed the data
-
When it was accessed
-
What changes were made
These records are analyzed by both internal security teams and automated monitoring systems to detect any anomalies or unauthorized activity in real time.
Encrypted Backups and Disaster Recovery
Phemex also maintains regular encrypted backups across multiple secure, geographically distributed locations. These backups ensure that user data remains available and recoverable even in extreme scenarios such as natural disasters, hardware failures, or cyberattacks.

KYC & AML (source)
Regulatory Compliance
Protecting user privacy also means respecting the laws that govern it. Phemex operates in compliance with global KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements.
-
Identity Verification and Data Integrity - Our compliance programs include robust identity-verification processes, where sensitive documents are securely uploaded, encrypted, and stored according to jurisdictional data-protection laws. All KYC data is handled under strict privacy protocols and never shared with third parties without user consent or lawful obligation.
-
Transaction Monitoring - Phemex’s compliance systems continuously monitor transactions for suspicious activity, protecting our community and broader ecosystem from fraud, money laundering, and other illicit behavior.
-
Cooperation with Regulators - As a responsible global exchange, Phemex works closely with financial authorities and compliance auditors to uphold the highest standards of transparency, accountability, and ethical conduct. In addition to meeting standard regulations, we aim to set new benchmarks for trust and safety in the crypto industry.
Conclusion
Security and privacy go hand in hand, which is why Phemex sees data safeguarding as a critical endeavor. Through end-to-end encryption, strict access policies, data isolation, constant auditing, and full regulatory compliance, we ensure that your personal and financial information stays under your control. When you trade with Phemex, you’re choosing a partner that values your privacy as much as your profits.
Want to learn more about how we keep you safe?