Symmetric key encryption, also called private key cryptography, is an encryption method where only one key is used to encrypt and decrypt messages. This method is commonly used in banking and data storage applications to prevent fraudulent charges and identity theft as well as protect stored data.

What Is Symmetric Key Encryption?
Symmetric key encryption relies on mathematical functions to encrypt and decrypt messages. The encryption is called “symmetric” because it uses a single key for both encryption and decryption. In comparison, asymmetric key encryption, also called public key cryptography, uses two separate keys to encrypt and decrypt messages.
A key is a random string of binary digits or bits created specifically to scramble and unscramble data. A key’s length and randomness are factors in determining a symmetric encryption algorithm’s strength. The longer and more unpredictable a key is, the harder it is for attackers to break the encryption by guessing the key.
A sender and their designated recipients have identical copies of the key, which is kept secret to prevent outsiders from decrypting their messages. The sender uses this key to encrypt their messages through an encryption algorithm, called a cipher, which converts plaintext to ciphertext. The designated recipients then use the same key to decrypt the messages by converting the ciphertext back to plaintext. For those without the key, the encrypted message would look like a series of random letters, numbers, and special characters.

Symmetric key encryption uses the same key for encryption and decryption. (Source: The SSL Store)
How Does Symmetric Key Encryption Work?
Modern computers don’t store data as alphabetic letters, instead, they keep everything as bits. Every character you type can be represented by an ASCII code, which is a combination of 8 bits.
Plaintext, ciphertext, and keys are all represented as binary digits on the computer. This makes it convenient for ciphers to utilize XOR, the “exclusive-or” logical operation, to encrypt and decrypt binary messages. XOR compares two input bits and generates a single output bit. If the bits in both inputs match, it returns false (i.e., 0). If they don’t match, it returns true (i.e., 1).
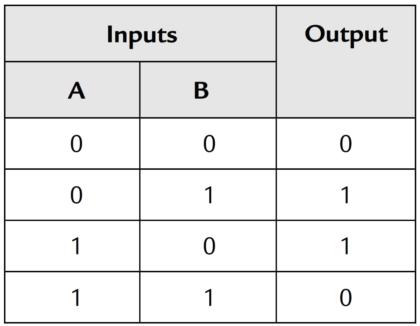
XOR truth table with the possible inputs and corresponding outputs (Source: Instrumentation Tools)
To send an encrypted message, a user would need to take their plaintext message and symmetric key as the input for the XOR. After comparing the two input bits via the XOR, the user will obtain the ciphertext as the output bit. Recipients can decrypt the message by reversing the encryption process. For decryption, recipients take the ciphertext and symmetric key as input for the XOR, and generate the original plaintext.
Example of A Symmetric Encryption
For example, suppose a sender wishes to send a message that consists of the word “Hi”:
- The sender and recipients share a 16-bit symmetric key, which is “01100010 01010000.”
- The message consisting of the word “Hi” is represented by “01001000 01101001” in binary.
- Comparing the two, the XOR returns an output of “00101010 00111001” which corresponds to “*9” after converting to text. This is the ciphertext.
- For decryption, the ciphertext is compared to the key to reobtain the plaintext message.
What Are the Categories of Symmetric Key Encryption?
Symmetric key ciphers are broken down into two main categories – block ciphers and stream ciphers. The two ciphers have different data encryption processes and operating environments.
Block Ciphers
This type of cipher breaks down plaintext messages into groups of bits (also called blocks) of predetermined sizes, and encrypts them into ciphertext. Block ciphers normally encrypt block sizes of 64 bits and above, and use keys of a fixed length of 56 bits, 128 bits, 192 bits, or 256 bits. The two most famous implementations of block cipher are as follows:
- Data Encryption Standard (DES) was developed in the early 1970s and is considered a legacy encryption algorithm. This block cipher used 56-bit keys and encrypted block sizes of 64 bits. Due to its short key length, the encryption standard was not very secure. However, it played a vital role in the advancement of cryptography. Because the US National Security Agency (NSA) participated in DES’s development, many academics were skeptical. This skepticism caused a surge in cryptography research, which led to the modern understanding of block ciphers.
- Advanced Encryption Standard (AES), also known as Rijndael, supersedes DES. AES is an encryption standard used by the US government to encrypt classified information. It is also popular with companies such as Google, Mozilla, and Microsoft. It is a family of block ciphers developed by the Belgian cryptographers Vincent Rijmen and Joan Daemen. The AES family can handle block sizes and encryption key sizes of 128, 160, 192, 224, and 256 bits. Officially, only 128-, 192-, and 256-bit key sizes and a 128-bit block size are specified in the encryption standard.
For an example of how a block cipher works, consider a 128-bit plaintext and a 128-bit key. The block cipher will split the plaintext into 8-bit blocks. During encryption, the cipher will compare the plaintext to the key block-by-block to produce the ciphertext. If the plaintext is less than 128 bits, the block cipher will employ a method called padding to reconcile the difference in block size. This method adds data to the beginning, middle, or end of the message prior to encryption. The added data depends on the padding scheme and can be nonsense phrases or used to obscure obvious messages. After decryption, the padded data is removed.
Other examples of block ciphers include Triple DES (3DES), International Data Encryption Algorithm (IDEA), and RC5. Block ciphers can also operate as stream ciphers through specific modes of operation such as Electronic Codebook (ECB), Cipher Block Chaining (CBC), and Counter (CTR).
Stream Ciphers
A stream cipher converts the plaintext in ciphertext bit-by-bit by breaking down plaintext messages into single bits and converting them individually. This cipher relies on a long stream of pseudorandom bits called a keystream. The keystream is generated by providing the encryption key and a seed to an internal algorithm (or keystream generator) which is an internal software. The seed is also called a nonce, which is a unique and randomly generated number that the cipher will use only once. Each message is encrypted and decrypted with different keystreams.
For the encryption and decryption of plaintext messages, each plaintext digit is encrypted one at a time with the corresponding keystream digit to return a ciphertext digit. A stream cipher is also called a state cipher, as the encryption of each digit depends on the current state of the cipher. There are two types of stream ciphers:
- Synchronous stream ciphersgenerate keystreams independently without relying on previous plaintext and ciphertext.
- Self-synchronizing stream ciphersdepend on previous ciphertext digits to generate keystreams.
The most widely-used stream cipher is Rivest Cipher 4 (RC4). RC4 keys are 64 bits or 128 bits in size. This cipher is easy to use, fast, and can work with large streams of data. RC4 encryption is used in common web protocols such as Secure Socket Layer (SSL), Transport Layer Security (TLS), and Wireless Equivalent Privacy (WEP). However, RC4 in its original form has severe vulnerabilities and can be cracked with relative ease. Its biggest weakness is its insufficient key schedule, where the first bytes of the output will reveal information about the key. A number of RC4 variants have been developed in efforts to try and resolve this issue, notably RC4A, Spritz, and VMPC.

What Are Symmetric Key Encryption’s Advantages?
Symmetric key encryption has two main advantages:
- Security: Symmetric key encryption is essentially unbreakable and requires users to keep track of only one key. In fact, the US government encrypts classified information with this method — specifically, the aforementioned AES implementation The most secure AES cipher has a 256-bit key size. Even with supercomputers, an attacker trying to brute forcethrough the encryption will need millions of years to crack it.
- Speed: Symmetric key encryption is simple in that it requires only one key of a relatively short length. As a result, it’s much faster to execute. It does not place a huge burden on a server during encryption and decryption, and can efficiently handle large amounts of data.
What Are Symmetric Key Encryption’s Vulnerabilities?
That said, symmetric key encryption system also has two notable weaknesses:
- Key distribution: To encrypt and decrypt messages, the sender and their recipients must share identical keys, so the sender must distribute the key in advance. The safest way is to distribute the key in person. If the two parties can’t meet face-to-face, they might send the key through the internet, which opens up the possibility of man-in-the-middle
- Key management: In symmetric key encryption, anyone with a key can decrypt the messages encrypted by that particular key. Through software-based attacks, attackers can gain access to keys kept in insecure locations, thereby compromising all encrypted messages. Keys also are regularly lost, making encrypted messages and data inaccessible.
Conclusion
Symmetric key encryption is a relatively secure, fast, and simple method of encrypting and decrypting large quantities of data without straining servers. Encryption and decryption are achieved using just one key, and anyone who has a key can decrypt all the messages encrypted by it. However, the distribution and management of this key are difficult and may create openings for attackers to steal the key and crack the encryption. Nevertheless, as long as the key is kept secret, symmetric key encryption is extremely secure. As such, it is still used as the standard encryption method of companies and governmental authorities worldwide.
Read More
- What is Blockchain Cryptography: The Backbone of Blockchain Security
- Bitcoin Public Key vs. Private Key: All You Need to Know
- Crypto Exchange Security in 2024
- What is Phishing in crypto & How to Prevent it?
- What is Sybil attack: How Blockchains Prevent Sybil Attacks
- Your 13-Point Crypto Security Checklist
- Efficient Market Hypothesis (EMH): Does Crypto Follow?
- What is Know Your Customer (KYC) and how does it work in Crypto?